What is Mod-security2 ?
ModSecurity2 is an open-source web application firewall (WAF) for Apache. It helps to protect web applications from a variety of attacks, including SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
Why We need to do this Mod-security2 ?
Implementing ModSecurity, or ModSecurity2, is beneficial for several reasons, especially when it comes to enhancing the security posture of web applications and protecting against various cyber threats. Here are some key reasons why organizations use ModSecurity:
- Protection Against Web Application Attacks: ModSecurity acts as a web application firewall (WAF), providing protection against a wide range of web application attacks, including SQL injection, cross-site scripting (XSS), and other common vulnerabilities. It helps to filter malicious traffic before it reaches the web application.
- Prevention of SQL Injection and Cross-Site Scripting: SQL injection and XSS are common attack vectors where attackers attempt to inject malicious code into web applications. ModSecurity can detect and prevent these types of attacks by analyzing and filtering incoming requests.
- Security Compliance: Many regulatory standards and security best practices recommend or require the implementation of a WAF for web applications. ModSecurity helps organizations achieve and maintain compliance with standards such as PCI DSS (Payment Card Industry Data Security Standard) and others.
- Real-time Monitoring and Incident Response: ModSecurity provides real-time monitoring of web traffic and logs security events. This allows security teams to analyze and respond to incidents promptly. The detailed logging helps in identifying the nature of attacks and understanding the security posture of the web application.
Security thread if i ignore Mod-security2
If your’re Ignoring ModSecurity2 then your web applications vulnerable to a range of security threats. Here are some potential security threats and risks associated with not using ModSecurity2:
- SQL Injection Attacks: Without a WAF like ModSecurity, your web applications may be susceptible to SQL injection attacks. Attackers can inject malicious SQL queries into input fields, potentially leading to unauthorized access, data manipulation, or data theft.
- Cross-Site Scripting (XSS) Attacks: XSS attacks involve injecting malicious scripts into web pages viewed by other users. Without protection, your applications may be vulnerable to these attacks, which can lead to session hijacking, defacement, or the theft of sensitive information.
- Cross-Site Request Forgery (CSRF) Attacks: CSRF attacks involve tricking a user’s browser into making unintended requests. ModSecurity can help detect and prevent these attacks by validating and blocking malicious requests.
- Security Compliance Violations: Many regulatory standards and compliance requirements mandate the use of a web application firewall. Ignoring ModSecurity may lead to non-compliance with standards such as PCI DSS, exposing your organization to potential legal and financial consequences.
Installation of ModSecurity:
sudo apt install libapache2-mod-security2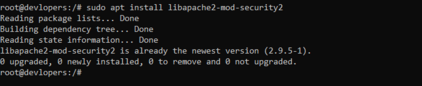
Run below code
sudo a2enmod security2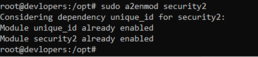
nano /etc/apache2/mods-enabled/security2.conf<IfModule security2_module>
# Default Debian dir for modsecurity's persistent data
SecDataDir /var/cache/modsecurity
# Include all the *.conf files in /etc/modsecurity.
# Keeping your local configuration in that directory
# will allow for an easy upgrade of THIS file and
# make your life easier
IncludeOptional /etc/modsecurity/*.conf
# Include OWASP ModSecurity CRS rules if installed
IncludeOptional /usr/share/modsecurity-crs/*.load
</IfModule>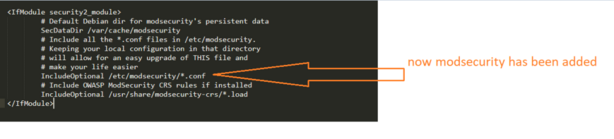
sudo mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf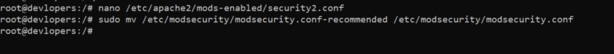
sudo nano /etc/modsecurity/modsecurity.conf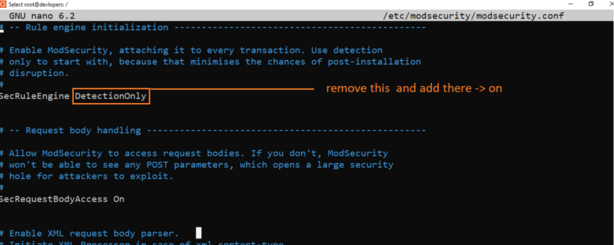
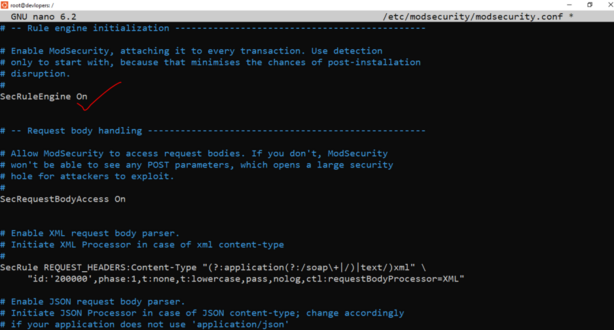
Thanks for learning. 👍👍